Through the source-level encryption technology, end-to-end video data encryption is implemented, and a more powerful and complete video security system is built. Based on the SVAC 2.0 standard research and establishment of the security system (as shown in Figure 1).
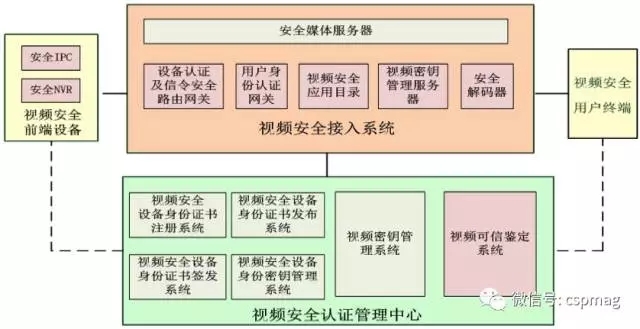
Fig.1 Schematic diagram of the safety system based on the SVAC2.0 standard
Video Security Front-End Equipment: Provides secure IPC and secure NVR device identity authentication, video capture encryption, and secure signaling control.
Video security user terminal: Complete functions such as on-demand broadcast of security video, on-demand on-demand broadcasting, and historical security video playback, and finally achieve normal playback of secure video. The video security user terminal implements security control such as video decryption and secure transmission through a hardware cryptographic module.
Video Security Certification Management Center: Provides basic key management services, including identity keys and video keys. Provide basic authentication certificates for devices and personnel, provide VKEK keys for video, and finally achieve video encryption and decryption functions.
Video security access system: Provides functions such as video surveillance front-end device registration, video transmission signaling control, real-time video on-demand, historical video playback, video storage, and video authentication, and finally implements digital certificate-based authentication and transmission of users and devices. The trusted authentication of the order, the credibility of the video data, and the encrypted transmission, storage, decryption, and playback of the video data ensure the security of the video surveillance network information.
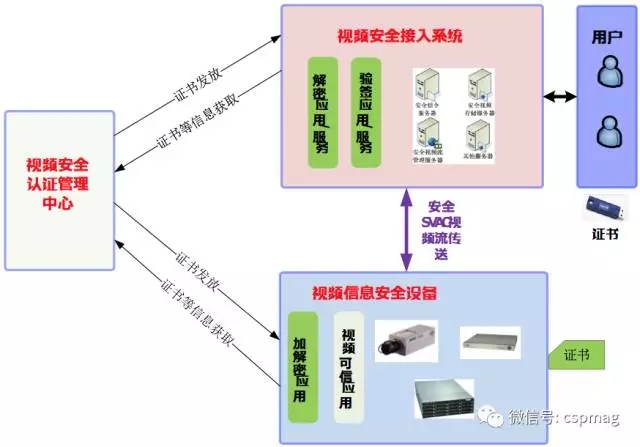
Figure 2 SVC2.0 based security system interaction diagram
The interaction diagram of the security system established based on the SVAC 2.0 standard is shown in Figure 2. The system adopts asymmetric and symmetrical cryptography technology and adopts digital signature and video encryption to verify whether the video content has been tampered with, thereby ensuring the confidentiality of the video content, preventing it from being illegally stolen and falsified, and satisfying the video networking information. The urgent need for security solves the problem of confidentiality and video data tamper protection during video data collection, transmission, storage, and playback in social security video surveillance systems.
Machinery And Equipment Parts,Metal Pipe Clips,Metal Tube Clamp,Clamp Metal
Ningbo Metal Sharing Supply Chain Management Co., Ltd , https://www.sharescm.com